For a while, fwupd has been able to verify the PCR0 checksum for the system firmware. The attestation checksum can be used to verify that the installed firmware matches that supplied by the vendor and means the end user is confident the firmware has not been modified by a 3rd party. I think this is really an important and useful thing the LVFS can provide. The PCR0 value can easily be found using tpm2_pcrlist if the TPM is in v2.0 mode, or cat /sys/class/tpm/tpm0/pcrs if the TPM is still in v1.2 mode. It is also reported in the fwupdmgr get-devices output for versions of fwupd >= 1.2.2.
The device checksum as a PCR0 is slightly different than a device checksum for a typical firmware. For instance, a DFU device checksum can be created using sha256sum firmware.bin (assuming the image is 100% filling the device) and you don’t actually have to flash the image to the hardware to get the device checksum out. For a UEFI UpdateCapsule you need to schedule the update, reboot, then read back the PCR0 from the hardware. There must be an easier way…
Assuming you have a vendor account on the LVFS, first upload the client certificate for your user account to the LVFS:
Then, assuming you’re using fwupd >= 1.2.6 you can now do this:
fwupdmgr refresh fwupdmgr update …reboot… fwupdmgr report-history --sign
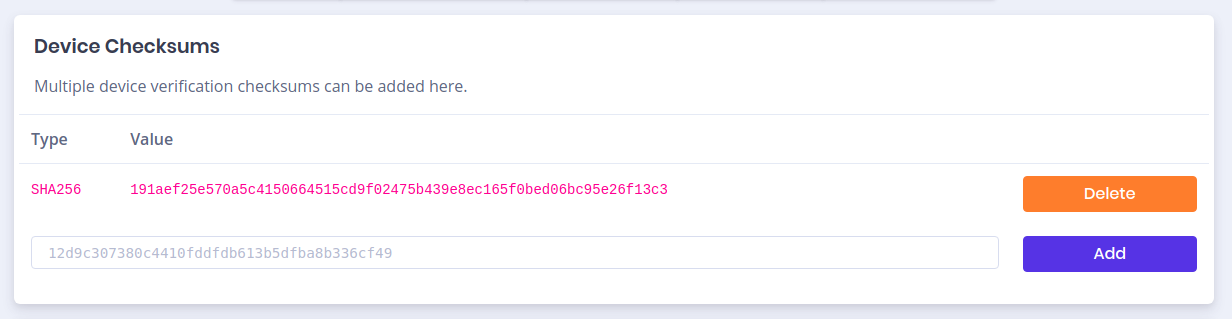
Notice the –sign there? Looking back at the LVFS, there now exists a device checksum:
This means the firmware gets the magic extra green tick that makes everyone feel a lot happier: