
Buy the T-Shirt
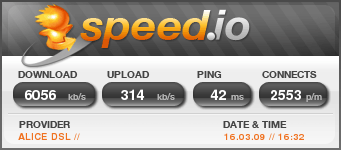
Well, I got curious how good my connection really is, so I did a (flash based) browser test on speed.io. The result is rather bad: 6MBit/s down and 300kBit/s up, while I pay for 16MBit/s down and 1MBit/s up.
I’ll move to Wilhelm.tel and pay a little more for 100MBit/s down and 5MBit/s up 🙂
I found a howto via forensikblog which wasn’t pretty good because it missed some details and installed CarvFS into your systems directories. You maybe want to have the carving files seperate from the rest of the system. So here comes a Howto Install CarvFS on your Ubuntu 8.10 machine:
cd /tmp/
sudo mkdir /opt/$USER/
sudo chown $USER:$USER /opt/$USER
mkdir /opt/$USER/carvfs
wget -O- 'http://downloads.sourceforge.net/ocfa/libcarvpath-0.2.0.tar.gz?use_mirror=mesh' | tar xvzf -
cd libcarvpath*
sudo apt-get install -y libsqlite3-dev libcurl4-openssl-dev
./configure --prefix /opt/$USER/carvfs && make && make install
cd /tmp/
wget -O- 'http://downloads.sourceforge.net/ocfa/carvfs-0.4.1.tar.gz?use_mirror=mesh' | tar xvzf -
cd carvfs*
sudo apt-get install -y libfuse-dev
export CFLAGS="-I/opt/$USER/carvfs/include/"
export LDFLAGS="-L/opt/$USER/carvfs/lib/"
./configure --prefix /opt/$USER/carvfs && make && make install
Happy Hacking
I have been at the CeBIT to represent GNOME. Actually, Herzi got sponsered by his generous employer, Lanedo, to make the GNOME booth happen. And he probably got bored that he called me up to do this together 🙂
We were in Hall 6, booth F60, sitting next to Drupal and some LDAP Webthing. Also, the KDE guys were next to us 🙂
They had awesome posters hanging on the walls, nice T-Shirts hanging around and banners showing off. They even came with name cards pinned on their chests and probably even with working hardware. The Drupal guys had a Roll-Up display and a foldable flyer holder with many information materials.
I envy those guys, because we haven’t had any of this stuff, besides a small computer and a monitor 🙁 There probably is something in GNOME Event Box, but unfortunately Herzi didn’t bring it, probably because it’s way too big and too heavy. Also, a roll-up display wouldn’t fit into that Box. Posters and banners would be nice, too. We even had to install an Ubuntu on the fair (instead of having it prepared beforehand). Then, the webcam didn’t want to work with cheese, so we couldn’t use that as an eye-catcher. Anyway, Sudoku and gnome-about were pretty good 😉 I believe, LinuxTag is going to be better, though. Because we have GNOMErs right there and you can transport things fast and easily, so it’s no big deal to replace a camera or a second PC.
Anyway, most of the time, we told the people, what GNOME is and automatically came to what a “desktop” is, what this “Open Source” thing is and what “Unix like systems” are. Some people actually had Linux experience and have a second (linux) partition, a VMWare or a server running linux.

We were also answering questions related to GNOME 😉 Users were asking what’s new in GNOME, how they use the accessibility stuff or the like. We used the chance of talking directly to users and asked what they like and dislike about GNOME. It turns out, that most of the time, the people are satisfied with their GNOME desktop, because it “just works” and it’s not in their way to achieve things. Also, they thought that the GNOME desktop is more light-weight than, e.g. the KDE desktop. Some people disliked that it looks a bit old-fashioned and that they can’t “play around” as much with their desktop as they are used to from, say, using windows. I told them, that it’s a design philosophy, to not have a huge (obvious) configuration space but to try to make it as easy as possible to do regular stuff. Of course, there is GConf where the about-to-be hackers can turn the nipples (and see the result instantly). I also tried to convert a few users to hackers: I even gave one guy “homework” to do… We’ll see how it turns out *g*
One guy asked me why he should choose GNOME over KDE. I avoided the whole discussion and gave no reason back. He should use what he likes and what fits his needs. Of course, I explained the philosophies behind GNOME and tried to make GNOMEy points.
Another one asked, whether there’s a “german GNOME community” and I sadly had to say “no”. But I hope, we Krauts can meet at LinuxTag and do that name-to-faces thing in a cosy restaurant. Maybe it’d be a good idea to pick one which has *no* WiFi or GSM/UMTS coverage, just to have no excuse to not talk to each other 😉
We pointed many people to our Wiki on live.gnome.org, especially the Roadmap or gnome-love. Let’s hope, they want to give some love to GNOME and fix some bugs 🙂
Of course, there were good parties at the end of the day, as well 🙂
I ordered some gagdets from focalprice.com, after read about that shop. I know dealextreme.com for quite some time now, but I’ve never dared to order something. And I’ve never heard about focalprice, which seems to be more or less the same shop anyway.
I’d say they delivered very fast. It just took 2.5 weeks to ship that stuff from Hongkong… Another interesting fact is, that German post delivered that as registered mail, which is positive, though.
Well then, I’m off playing with my new gadgets 😉
Matthew Dempsky found a bug in TinyDNS and the author, Daniel Julius Bernstein, has a Security Guarantee that rewards the first who finds an exploitable bug with $1000 and he says, he is going to make it happen! I love this guy…
The problems I described last time, are gone now 🙂 The paramiko mailinglist is, besides the pretty good documentation, a very good information ressource.
So I built a Fon client in Python which allows you to login to the Fon server and make your Fonera officially online.
So in order to get your copy of PyFON, do a
hg clone http://hg.cryptobitch.de/pyfon
To use it, simply give the MAC address of your Foneras wireless interface as an argument and run it or do it in a more sophisticated way:
muelli@xbox:~/hg/pyfon$ python ./src/pyfonclient.py --loglevel info --firmware 0.7.2 --revision 3 --mode cron --ethernetmac 00:18:84:fo:ob:ar 00:18:84:fo:ob:ar INFO:root:Connecting to host: download.fon.com:1937 as user: openwrt INFO:paramiko.transport:Connected (version 2.0, client OpenSSH_4.3p2) INFO:paramiko.transport:Authentication (publickey) successful! INFO:root:Connect finished INFO:paramiko.transport:Secsh channel 1 opened. INFO:root:Found _auth_string: mode='cron' wlmac='00:18:84:ff:ee:dd' mac='00:18:84:fo:ob:ar' fonrev='3' firmware='0.7.2' chillver='1.0-1' thclver='1.0' device='fonera' INFO:root:Finally closing everything muelli@xbox:~/hg/pyfon$
If you increase the loglevel to, say, debug, then you’ll get the script which Fon send you and supposes you to execute. If you change your password via the Fon webinterface, you’ll see your new password in that script.
So if you want to disturb the Fon network, you can iterate over all Fon MACs and receive the possible made configuration changes. By that, you’ll get the new passwords as well, of course…
Another funny thing is that the Fon server sends you their banner, if you explicitely request a shell:
In [1]: import pyfonclient In [2]: c = pyfonclient.Client() In [3]: c.connect() In [4]: channel = c.client.invoke_shell() In [5]: channel.recv_ready() Out[5]: True In [6]: buf="" In [7]: while channel.recv_ready(): buf += channel.recv(1) ...: In [8]: print buf Linux fonesfat02 2.6.18-6-amd64 #1 SMP Sun Feb 10 17:50:19 UTC 2008 x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. In [9]:
But you can’t execute any command…
Patches are, as always, welcome 🙂
You might know that FON thing, which basically provides you with WiFi on many places. They give you an access point which they suppose you to run and provide that WiFi to others. Then you are eligible to use other peoples WiFi.
The given access point connects itself with a script to the main server and tells it, that it’s online. The server then grants you access to other WiFis.
If you flash the access point, which is called “fonera”, with e.g. OpenWRT then you’ll lose that script. This in pretty bad because you *do* provide free WiFi to the people (unless you don’t run an open WiFi) but lose the right to use others.
There are sites out there which describe, howto do the “heartbeat” yourself, but they have major drawbacks:
Also note, that you can receive the files from the Fon development site and steal that heartbeat thing from there.
Thanks to this site I found a way to convert the dropbear key to the OpenSSH format (/usr/lib/dropbear/dropbearconvert dropbear openssh fonkey fonkey.ssh), but that bash thing is still ugly. Also, to use OpenSSH, you have to fiddle with permissions of the keyfile, etc.
So in order to run that heartbeat thing properly on, say, your PC, you don’t want to depend on dropbear or “nvram” to get the MAC address of your wireless interface. You might want to run the following script, of course you have to adapt the variables first. I try to get rid of Bash, but I still have a few problems with Pythons SSH package: I can’t send something to “stdin”, like “echo 'foo' | ssh bar” does.
#!/bin/sh
#
# version 1.1.0
THINCLIENTPATH="/tmp" # path of this file
ROOTHOME="/tmp/root" # root's home dir
SSHPATH="/usr/bin/ssh" # path to ssh
KEY="/tmp/fonkey.ssh.1" # private key for fetching the info from the FON server
THINCLIENTOUT="/tmp/.thinclient.sh" # output file
THINCLIENTOUTDEFAULT="33" # default size of the output file
THCLVER="1.0"
CHILLVER="1.0-1"
FONREV="2" # /etc/fon_revision
FIRMWARE="0.7.2" # taken from /etc/banner (without Beta)
DEVICE="fonera"
USER="openwrt"
SERVER="download.fon.com"
PORT="1937"
FONSIG="$SERVER ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAIEA0zJFtj5NtrVsj8+qG0dtPE8WpHHDpTXp5+d3vvtSS7Hx7vYHyrfN/8PBVrrYOgl4dySY65sGtq34EU04VN4a7xQHSKJBunDUSQ/2Xz+eyo53LCVeFy1zNRCmB6jrFlJQvl5yviLvXmMtOGxG8Z1dfu4qavfGtBxwtwxKPKuiyhs="
cat > $KEY <> $ROOTHOME/.ssh/known_hosts
}
exec_cron_mode () {
check_env
sleep "$((0x$(head /dev/urandom |hexdump |awk '$2 > 0 {print $2}'|head -n1) % 10))"
echo "mode='cron' wlmac='$MAC' mac='$ETMAC' fonrev='$FONREV' firmware='$FIRMWARE'" | $SSHPATH -T ${PORT:+ -p $PORT}${KEY:+ -i $KEY} "${USER}@${SERVER}" > $THINCLIENTOUT
echo "sent: mode='cron' wlmac='$MAC' mac='$ETMAC' fonrev='$FONREV' firmware='$FIRMWARE'"
exec_check_thinclient
}
exec_start_mode () {
sleep 10 # make sure WAN is up and crond is running
check_env
[ -f "/tmp/crontab" ] || touch /tmp/crontab
[ `grep -c thinclient /tmp/crontab` = "0" ] && echo "24,54 * * ** root $THINCLIENTPATH/thinclient cron > /dev/null 2>&1 &" >> /tmp/crontab
echo "mode='start' wlmac='$MAC' mac='$ETMAC' fonrev='$FONREV' firmware='$FIRMWARE' chillver='$CHILLVER' thclver='$THCLVER' device='$DEVICE'" | $SSHPATH -T ${PORT:+ -p $PORT}${KEY:+ -i $KEY} "${USER}@${SERVER}" > $THINCLIENTOUT
echo "sent: mode='start' wlmac='$MAC' mac='$ETMAC' fonrev='$FONREV' firmware='$FIRMWARE' chillver='$CHILLVER' thclver='$THCLVER' device='$DEVICE'"
exec_check_thinclient
}
exec_check_thinclient () {
if [ -f $THINCLIENTOUT ]
then
THINSIZE="$(wc -c < $THINCLIENTOUT)"
if [ $THINSIZE = "0" ]
then
echo "Something is wrong, $THINCLIENTOUT is empty"
elif [ $THINSIZE != "33" ]
then
echo "Something is different in $THINCLIENTOUT:"
cat $THINCLIENTOUT
else
echo "$THINCLIENTOUT is the default one, deleted"
rm $THINCLIENTOUT
fi
else
echo "Something is wrong, $THINCLIENTOUT does not exist!"
fi
}
case "$1" in
cron)
exec_cron_mode
;;
start)
exec_start_mode
;;
check)
exec_check_thinclient
;;
*)
echo "Usage: `basename $0` {cron|start|check}"
exit
esac