Again, I had the great pleasure to attend the annual DFN Workshop which takes place in the Conference Center Hamburg (ever thought about, why they haven’t called it “Konferenz Zentrum”?).
It’s more “tieish” than a Chaos Communication Congress but it’s still comfortable being there. Most people have a strong academic background so they were used to jeans and pullovers as well 😉
The first person to speak was a Dr. Neil Long from Team Camry and he spoke about the underground economy. They claim to research and investigate in that area and make deals with the criminals. He showed IRC logs most of the time and it was quite funny to see how the people interact with each other. They actually do speak 1337 and even I had a tough time reading their conversation 😉 He explained in great detail how the underground is organized. He claimed, that there are specialists for everything, everywhere. Programmers, Exploit-writers, Webhosts, Credit Card stealers, yadda yadda. Everything has it’s price and that is paid through various online money trasferring systems.
The next guy talked about Exploit Toolkits for the Web. He named various kits, like MPack, IcePack, NeoSploit, FirePack or UniquePack. They basically allow you to create a drive-by download site and deploy a given payload. The programs itself are split up into two parts. A server part which actually exploits a browser and makes it download and execute a loader program which in turn downloads the second stage – the real malware to be run on the victims machine. The other part is a binary to create that first-stage program. I spent some time in searching for those toolkits and downloaded some of them. That required me to learn some Russian 😉
This first-stage part opens an interesting attack vector to the wannabe hackers: Many Web Exploit Toolkits were infected with malware themselves. Because you have to run a strange smelling binary to create your first-stage excutable, you might run foreign malware yourself. I actually don’t understand, why this loader thing is such a big issue. I assume you could deploy your malware in first place without having it loaded through a staging program.
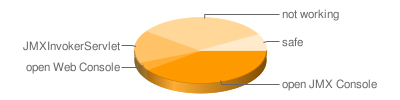
The next interesting talk was given by the smart guys from Red Team Pentesting, which is a pretty interesting company actually. Former students founded that company and they do professional Pentesting. I have to admit, that I envy them a little. It must be a great job with a lot of interesting stuff to see. Anyay, they talked about jBoss insecurities. It seems that jBoss comes with development configuration and the people don’t change them to productive values but blindly bind their server to the network. It turns out that you can get shell access through nearly a handful ways, even if a smart administrator has locked some ways down. Also, many corporate or governmental site are driven by a jBoss server and -which is the interesting part- have a weak configuration. They have an interesting statistic that shows that only 8% of the JBoss servers out there are reasonably secure.
I was actually bored by just one talk. It was about GRID Firewalls. While the topic is interesting in general, the guy made me fall asleep :- That’s a pity, because I believe he knew what he was talking about and had valuable information to deliver, especially due to his strong emphasis on practical problems. Maybe he can get his talk accepted next year and improve his talking skills.
After the first day, we visited the Groeninger Braukeller which was a real blast! They have one of the finest beers I know of. Also the food in there is delicious. It’s a perfect atmosphere to get together and discuss the talks you’ve just listened to. I also took the chance to meet old friends which I haven’t seen for a while.
Probably due to the massive amount of food and beer, I couldn’t sleep well that night and I thus was very tired the second day. I’ve listened to the talks but I couldn’t make it to the ModSecurity workshop 🙁 It’s really annoying, because I actually wanted to attend that session! I do use ModSecurity at some projects and I think it’s a good tool. A reallife-relevant workshop would have been great.
So, if you have nothing else to do on 2009-02-09, consider coming to Hamburg and enjoy the 17th DFN Workshop!