Again, this is a quick reminder for myself and I want to share it with you.
There is an interesting webservice which tracks nearly all your (read: mine) parcels. It also offers an RSS feed and maps 🙂
The service is available under http://boxoh.com/
Again, this is a quick reminder for myself and I want to share it with you.
There is an interesting webservice which tracks nearly all your (read: mine) parcels. It also offers an RSS feed and maps 🙂
The service is available under http://boxoh.com/
Bald sind Bundestagswahlen und Blumentopf moechten dich mit einem Video zur Wahl motivieren:
Und zur Entscheidungsfindung empfehle ich Rette deine Freiheit, ein wirklich sehr gelungenes Video:
Aber Obacht: Die offensichtliche Empfehlung, die FDP zu waehlen, ist nicht vor dem Hintergrund einer schwarz-gelben Koalition nicht schlau, denn die FDP hat angekuendigt, nur gegen das Zensurgesetz vorzugehen, wenn sie nicht an der Regierung beteiligt sind. Aber auch sonst gaebe es mit der FDP nicht so viel zu lachen.
Eine andere Entscheidungshilfe kann die Uebersicht der Free Software Foundation Europe (FSFE) sein: Auf einer Wikiseite werden Positionen der Abgeordneten zu Freier Software gesammelt. Ein sehr interessantes Projekt.
Noch ein schoenes Video vom selben Macher ist Du bist Terrorist:
Wenn du den Film gut findest, dann vote fuer ihn im Bitfilmfestival Voting!
Wir haben die Kraft! Unser Land kann mehr!
PS: Sorry fuer das einbinden von YouTube, wenn du eine freie Alternative kennst, sag bescheid!
Hier der Trailer zur geplanten Großdemonstration unter dem Motto “Freiheit statt Angst – Stoppt den Überwachungswahn!“, die am 12.09.2009 in Berlin stattfindet. Hinweise zur Anfahrt gibt es im FoeBud Blog.
Die Forderungen der Bürgerrechtler sind:
1. Überwachung abbauen
- Abschaffung der flächendeckenden Protokollierung der Kommunikation und unserer Standorte (Vorratsdatenspeicherung)
- Abschaffung der flächendeckenden Erhebung biometrischer Daten sowie von RFID-Ausweisdokumenten
- Schutz vor Bespitzelung am Arbeitsplatz durch ein Arbeitnehmerdatenschutzgesetz
- Berücksichtigung des Datenschutzes für Bürger- und Arbeitnehmer/innen bereits in der Konzeptionsphase aller öffentlicher eGovernment-Projekte
- Keine einheitliche Schülernummer (Berliner SchülerID)
- Keine Weitergabe von Informationen über Menschen ohne triftigen Grund
- Keine europaweite Vereinheitlichung staatlicher Informationssammlungen (Stockholmer Programm)
- Keine systematische Überwachung des Zahlungsverkehrs oder sonstige Massendatenanalyse in der EU (Stockholmer Programm)
- Kein Informationsaustausch mit den USA und anderen Staaten ohne wirksamen Grundrechtsschutz
- Abbau von Videoüberwachung und Verbot des Einsatzes von Verhaltenserkennungssystemen
- Keine pauschale Registrierung aller Flug- und Schiffsreisenden (PNR-Daten)
- Keine geheime Durchsuchung von Privatcomputern, weder online noch offline
- Keine Einführung der Elektronischen Gesundheitskarte in der derzeit geplanten Form
2. Evaluierung der bestehenden Überwachungsbefugnisse
Wir fordern eine unabhängige Überprüfung aller bestehenden Überwachungsbefugnisse im Hinblick auf ihre Wirksamkeit, Kosten, schädliche Nebenwirkungen und Alternativen.
3. Moratorium für neue Überwachungsbefugnisse
Nach der inneren Aufrüstung der letzten Jahre fordern wir einen sofortigen Stopp neuer Gesetzesvorhaben auf dem Gebiet der inneren Sicherheit, wenn sie mit weiteren Grundrechtseingriffen verbunden sind.
4. Gewährleistung der Meinungsfreiheit und des freien Meinungs- und Informationsaustauschs über das Internet
- Keine Beschränkung des Internetzugangs durch staatliche Stellen oder Internetanbieter (Sperrlisten)
- Keine Sperrungen von Internetanschlüssen
- Verbot der Installation von Filtern in die Infrastruktur des Internet.
- Entfernung von Internet-Inhalten nur auf Anordnung unabhängiger und unparteiischer Richter.
- Einführung eines uneingeschränkten Zitierrechts für Multimedia-Inhalte, das heute unverzichtbar für die öffentliche Debatte in Demokratien ist.
- Schutz von Plattformen zur freien Meinungsäußerung im Internet (partizipatorische Websites, Foren, Kommentare in Blogs), die heute durch unzureichende Gesetze bedroht sind, welche Selbstzensur begünstigen (abschreckende Wirkung)
After ranting about the HanseNet Speed, I now have the opponents test result: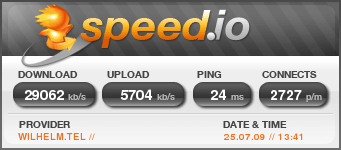
I didn’t expect 100MBit/s down, because I still have my old router in place which most likely isn’t able to push 100MBit/s. I’ll definitely give it a new try once I am “directly” connected, i.e. without any unnecessary hardware in between.
Again, I had the great pleasure to attend the annual DFN Workshop which takes place in the Conference Center Hamburg (ever thought about, why they haven’t called it “Konferenz Zentrum”?).
It’s more “tieish” than a Chaos Communication Congress but it’s still comfortable being there. Most people have a strong academic background so they were used to jeans and pullovers as well 😉
The first person to speak was a Dr. Neil Long from Team Camry and he spoke about the underground economy. They claim to research and investigate in that area and make deals with the criminals. He showed IRC logs most of the time and it was quite funny to see how the people interact with each other. They actually do speak 1337 and even I had a tough time reading their conversation 😉 He explained in great detail how the underground is organized. He claimed, that there are specialists for everything, everywhere. Programmers, Exploit-writers, Webhosts, Credit Card stealers, yadda yadda. Everything has it’s price and that is paid through various online money trasferring systems.
The next guy talked about Exploit Toolkits for the Web. He named various kits, like MPack, IcePack, NeoSploit, FirePack or UniquePack. They basically allow you to create a drive-by download site and deploy a given payload. The programs itself are split up into two parts. A server part which actually exploits a browser and makes it download and execute a loader program which in turn downloads the second stage – the real malware to be run on the victims machine. The other part is a binary to create that first-stage program. I spent some time in searching for those toolkits and downloaded some of them. That required me to learn some Russian 😉
This first-stage part opens an interesting attack vector to the wannabe hackers: Many Web Exploit Toolkits were infected with malware themselves. Because you have to run a strange smelling binary to create your first-stage excutable, you might run foreign malware yourself. I actually don’t understand, why this loader thing is such a big issue. I assume you could deploy your malware in first place without having it loaded through a staging program.
The next interesting talk was given by the smart guys from Red Team Pentesting, which is a pretty interesting company actually. Former students founded that company and they do professional Pentesting. I have to admit, that I envy them a little. It must be a great job with a lot of interesting stuff to see. Anyay, they talked about jBoss insecurities. It seems that jBoss comes with development configuration and the people don’t change them to productive values but blindly bind their server to the network. It turns out that you can get shell access through nearly a handful ways, even if a smart administrator has locked some ways down. Also, many corporate or governmental site are driven by a jBoss server and -which is the interesting part- have a weak configuration. They have an interesting statistic that shows that only 8% of the JBoss servers out there are reasonably secure.
I was actually bored by just one talk. It was about GRID Firewalls. While the topic is interesting in general, the guy made me fall asleep :- That’s a pity, because I believe he knew what he was talking about and had valuable information to deliver, especially due to his strong emphasis on practical problems. Maybe he can get his talk accepted next year and improve his talking skills.
After the first day, we visited the Groeninger Braukeller which was a real blast! They have one of the finest beers I know of. Also the food in there is delicious. It’s a perfect atmosphere to get together and discuss the talks you’ve just listened to. I also took the chance to meet old friends which I haven’t seen for a while.
Probably due to the massive amount of food and beer, I couldn’t sleep well that night and I thus was very tired the second day. I’ve listened to the talks but I couldn’t make it to the ModSecurity workshop 🙁 It’s really annoying, because I actually wanted to attend that session! I do use ModSecurity at some projects and I think it’s a good tool. A reallife-relevant workshop would have been great.
So, if you have nothing else to do on 2009-02-09, consider coming to Hamburg and enjoy the 17th DFN Workshop!
Last Friday, 5 major ISPs signed a contract to commit themselves to forge DNS answers for names given by the federal police.
According to this article (which probably has it’s information from heise) Deutsche Telekom, Vodafone/Arcor, Hansenet/Alice, Telefonica/O2 and Kabel Deutschland are voluntarily implementing the censorship through DNS. The signing parties share 75% of the german ISP market. According to Netzpolitik.org, Freenet, 1&1 and Versatel have denied to even talk about this censorship if there isn’t a legal foundation, i.e. a law which explicitly requires the ISPs to implement the censorship. While I don’t know the contract and according to the press conference, it remains secret. But it must be more or less like the leaked draft.
So the ISPs now have to implement DNS filter within six months and have to update the filter as soon as the federal police sends them a new list of to be blocked domains. The weird and absurd thing is, that *nobody* is allowed to access this list (because illicit content is explicitly referenced)! So you can’t control what exactly is banned and whether political enemies are censored as well. So it happened in Finland: A site, discussing the censorship, is on the list itself!
In the same period Wikileaks published the Finnish Internet censorship list. The Finnish National Bureau of Investigation has requested executive assistance from United States, but it is not known what precisely has been requested – whether the concern is only removing the list or whether they are trying to find out who leaked it. The list still includes the critical Finnish anti-censorship site lapisporno.info.
But, making it harder to access “child pornography” justifies the restriction of the constitutional rights, right? Well. Firstly, we mustn’t use “child pornography” when we want to discuss this issue seriously. We should use “documentation of child molesting” or something more technical. Secondly, we see, that it’s pretty simple to circumvent thus it’s only slightly harder to access the desired information. So it helps pretty much nothing in blocking the access, *but* offends 75% of the german internet population. I don’t consider this proportionate!
But the less a person watches children being molested, the less children she’ll molest, right? Because they get addicted and everything… Well. Besides the fact that we’re talking about a sexual disposition and not about drugs of any kind, this is just a claim with no justification whatsoever. An equally good argument is, that doing that virtually actually *prevents* people from doing that in real life. Also, the content available on the net is decades old, which might testify, that there is no need to produce more and thus newer content! By actually blocking access, you might risk people demanding newer stuff and a big market emerges.
Also, no child is molested through the internet. This is probably always done in the families! So blocking access doesn’t save a single child. Instead, fighting the roots would help. scusi analysed, where the blocked domains are actually hosted. It turns out, that pretty much every blocked domain is in a legislation that allows prosecution of child abuse. Including various servers in Germany! I propose, that it’s easier, more effective and less dangerous to actually ask the ISPs to shut the domains down and to prosecute the owners of these sites. Instead, the attitude of “once it’s blocked, we don’t have to care about anymore” is encouraged. Of course that doesn’t help anything, because the content is *still there* and people can circumvent cencorship to access it!
It is obvious, that other interest groups, like the music industry, will ask and fight for adding sites they don’t like to that blocking list. The technical implementation doesn’t and can’t know what’s “right” and what’s “wrong”. It blocks what it’s told to. So with that censorship being deployed, you introduce a general censor mechanism for pretty much everything you desire. Today it’s child pornography, but it is clear that this’ll change, like e.g. in Australia where a dentist has been blocked as well…
While I tried to argue against the official reasons for the “access blocking”, other people did it as well. There is a good article at Netzpolitik, which actually destroys nearly every exiting argument. Of course, heise has a pretty good article, too, which I really urge you to read.
What now? Well, first of all, you can quit your current contract with your ISP or sue them. Then you can use alternative dns server. As of writing, the list includes
Of course, the parliament has free access and universities shall have unlimited access, too, so you might want to use their DNS servers as well, e.g. 132.187.1.1 or 129.187.5.1.
But again: The point is not, that the technical measure is nearly useless to filter content. The point is that censorship infrastructure is rolled out *now* and that it can (and my prophecy is, that it will) be (ab)used for other content as well.
For further information, there is herdict.org which maps the current cencorship situation worldwide. For Germany, you might want to have a look at de-zensiert.de or ak-zensur.de.
What about a consensus DNS resolver you install locally? It would ask, say, three different DNS servers and responds with the answer given the most. It could show a warning widget if it recognizes inconsistencies or if a DNS server fails to answer. The user then knows, that something’s fishy and can act appropriately, i.e. update the DNS server list or ask his provider whether it censors.
To summarize: The current child pornography histeria is based on assumptions that are evidently wrong or can’t be proved. The methods to fight against child abuse have no meaningful effect besides deploying a general purpose censoring infrastructure (and help the people involved to improve their public image). Nobody is allowed to check whether the access block list includes any non illegal entry and political enemies can thus be eliminated. Circumventing is (still?) easy. We can further improve anti blocking mechanisms.
*Yay*! Armor Games released Gem Craft 2 – Chapter 0! I absolutely loved Gem Craft 1 and I couldn’t wait for the next round of that fabulous game. I don’t do much games on my computer in general as I have much better things to do, but I couldn’t stop playing Gem Craft.
It’s a fantastic Tower Defence with nice sounds, graphics and an amazingly entertaining gameplay. The major drawback is, that it’s flash based 🙁 (I wonder whether one could make swfdec to save the state of a flash game, like a virtual machine in QEmu…) I haven’t tried the new game extensively yet, but I’m sure that this game will cost me the next weekends 😉
If you like Tower Defence games, you’ve got to try CreepSmash as well. It’s an open and free multiplayer Tower Defence written in Java. It lacks nice graphics and sounds (and security 😉 ) but it’s definitely amusing to plan and play against other (real) player.
Happy playing!
If you happen to live in Germany and incidentally like chocolaty things, you might already have seen that you are eligible to download 20 MP3 files, with every bigpack Hanuta you buy. At least that’s what the ads say.
You are supposed to visit http://www.20songsgratis.de/ which doesn’t even run properly in my browser. It demands JavaScript, but even if you allow JavaScript for three domains, it wants to run a flash file… After managing that, I was supposed to download and execute a strange Win32 binary. I was fed up and I searched for a contact address. I didn’t succeed in first place, but as I know that Hanuta is made by Ferero, I searched their website. The webform didn’t accept my email address because it thinks that “+” is an illegal character for email addresses *sigh*.
So I wrote that I assumed I could download MP3s somewhere but it’s not possible because they only offer a strange smelling binary and how I could get my music now. Of course they have to give it to me because they advertised it and didn’t say what is needed to get them.
After a few days, a nice woman called me and was very sorry that this MP3 thing doesn’t run with Linux and next time they’ll look after it and she was again very sorry. Then she offered me a chocolate package as kind of a refund ^^ Of couse I didn’t say no *yummie*
So, if you got this Linux thing and want some chocolate, go out and buy these Hanuta packs and complain to Ferero 😉 It’ll also help to bring Linux to the peoples mind.
I got my result from the DAAD after I have been there a few weeks ago!
Turns out, I won’t get the stipend, but I am on kind of a list, if anybody drops out. I consider that rather unlikely so I’ll concentrate on other methods to get some money. By the way: If you have some spare money and don’t know what to do with it, consider giving it to me 😉
Anyway, I still need a language test from IELTS before I can apply at the DCU and start looking for a space to live.